Security tools often operate like black boxes. They scan, they analyze, and they produce a list of vulnerabilities — but the underlying evidence remains hidden.
We believe security should be different.
At Chowkidar, every reported vulnerability is backed by the raw scan data generated while analyzing your defined scope. No assumptions. No invisible logic. Just verifiable evidence. Because trust in security doesn’t come from claims — it comes from proof.
No Black Boxes - Only Evidence
When Chowkidar scans your scope, it collects detailed technical output directly from the scanning process. This includes:
- Endpoint discovery results
- Service detection outputs
- Response headers and configurations
- Misconfiguration indicators
- Behavioral observations
- Technical artifacts that led to detection
This raw data forms the foundation of every vulnerability we report. If we flag an issue, the underlying evidence is available. You can see exactly what triggered the finding.
Built for Researchers Who Demand Proof
Security researchers and internal security teams often want more than a summary. They want to validate findings, reproduce behavior, and perform deeper analysis. By providing access to the raw scan data, Chowkidar enables independent verification and technical scrutiny.
This transparency empowers teams to confidently assess risk, confirm accuracy, and collaborate more effectively on remediation.
From Evidence to Vulnerability
Every vulnerability reported by Chowkidar follows a clear, defensible path. The scanner collects real-time technical data from the scoped assets, analyzes patterns and misconfigurations, and maps validated evidence to known vulnerability categories. The result is not a guess or a probability score alone — it is a finding backed by measurable technical proof.
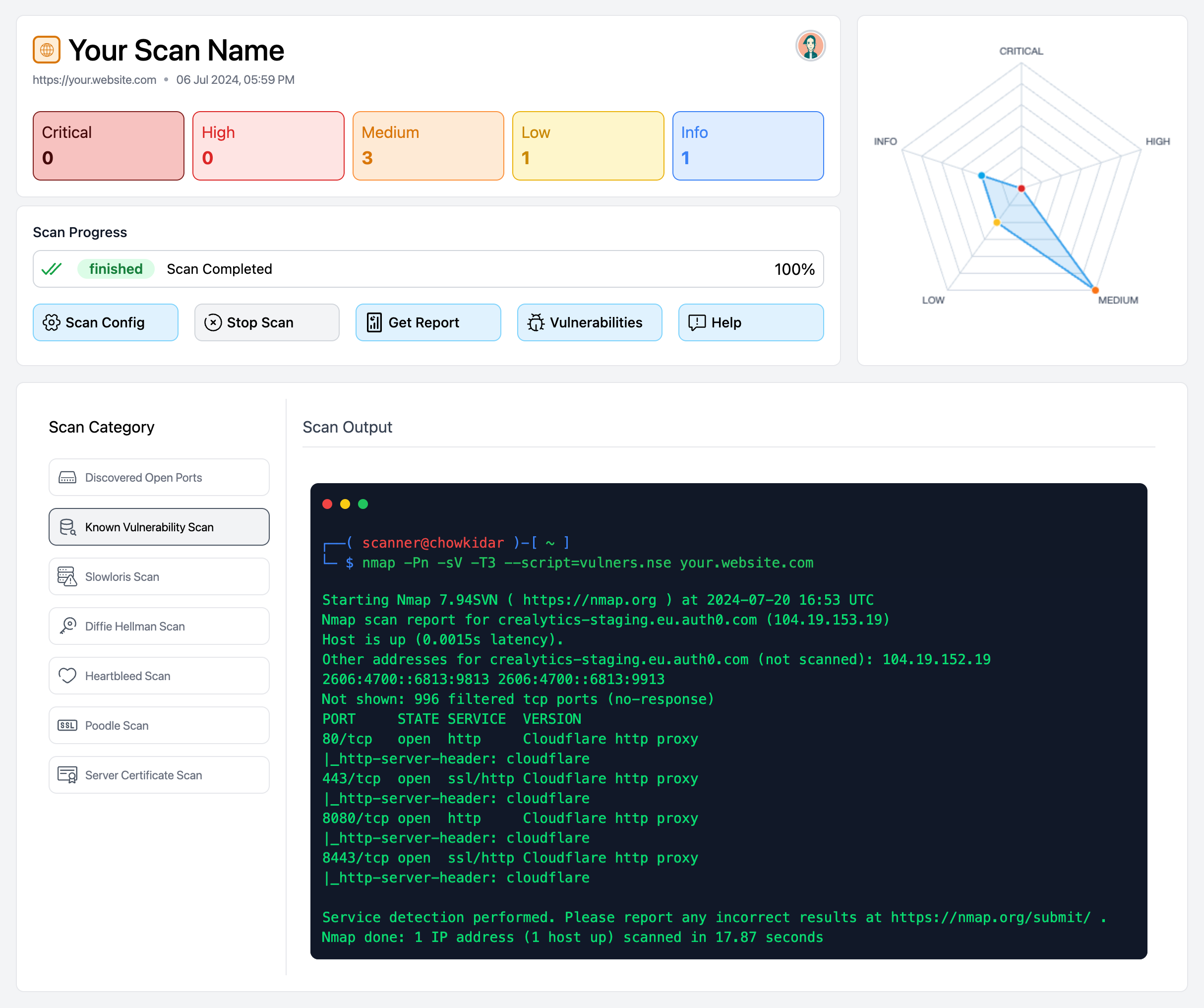
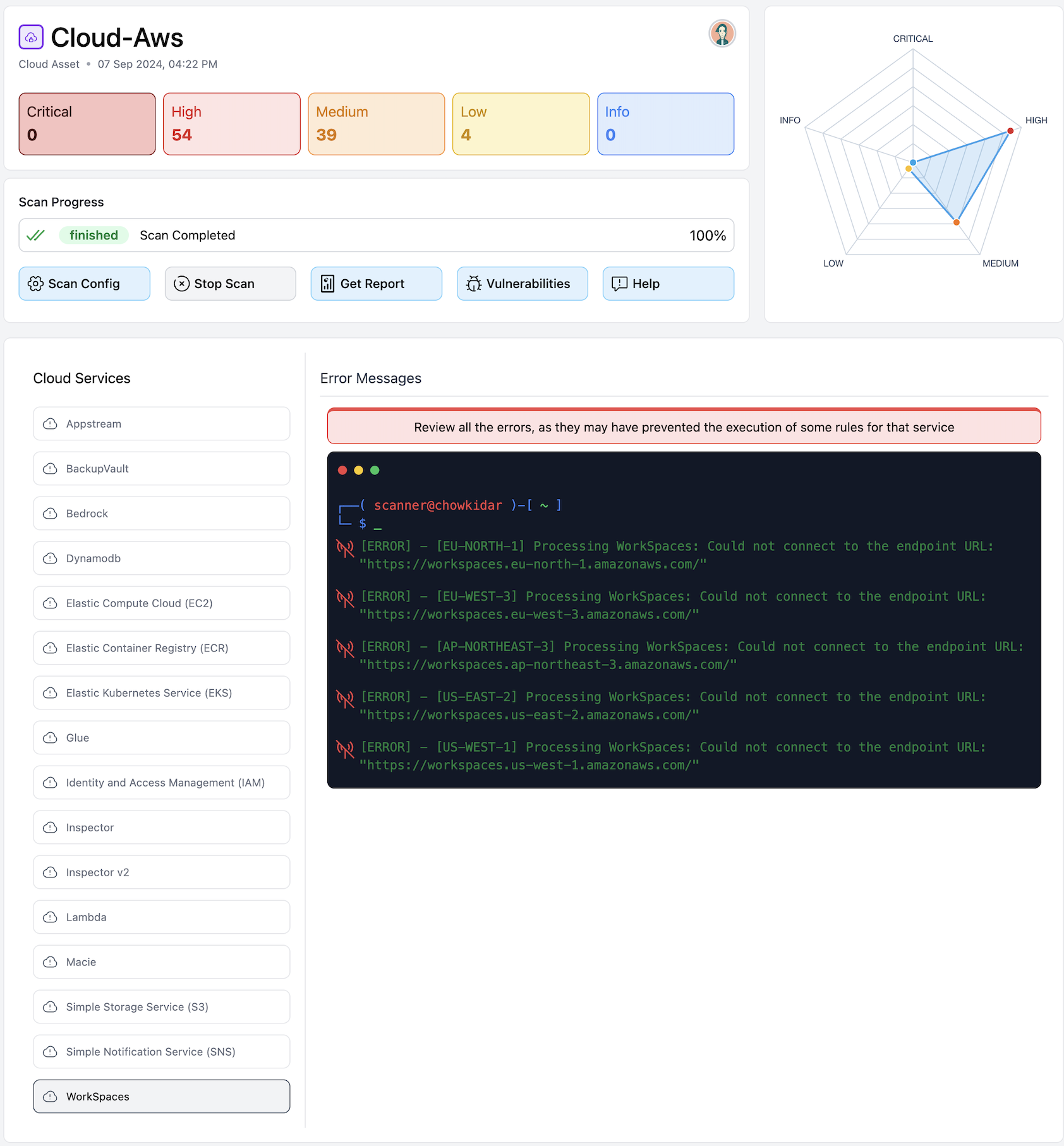
Security You Can Verify
In an era where automation and AI drive much of modern security tooling, transparency is often sacrificed for convenience. Chowkidar was built on a different principle: visibility builds trust.
By exposing the raw data behind every vulnerability, we ensure that our security reports are not just informative — they are defensible, reviewable, and grounded in evidence.
Because real security doesn’t rely on blind trust. It earns confidence through transparency.
